Introduction
starttls is an extension of a plaintext communication protocol, enabling a clear communication connection to encryption (encryption using SSL or TLS) ), Without the need to use another special port to make encrypted communication, belongs to opportunities.
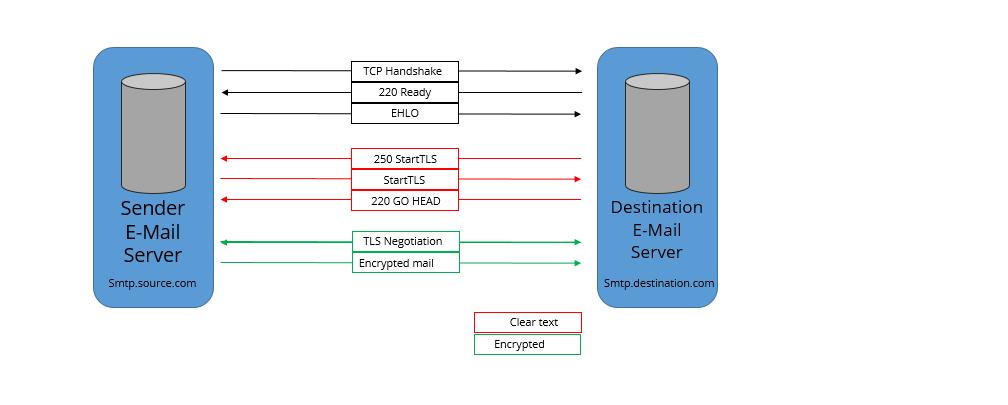
StartTLS itself is an agreement with an application layer that can be operated with many application layer protocols. Use StartTLS in IMAP and POP3, is defined in RFC 2595. Used in SMTP, defined in RFC 3207, used in FTP, defined in RFC 4217. Use in XMPP to define in RFC 6120. Used in LDAP, in RFC 2830, in NNTP, in RFC 4642.
Opportunity Encryption
Opportunity Encryption or Plastic Encryption (English: Opportunistic Encryption, Abbreviation OE ; sometimes called Non-authentication encryption , Random encryption ) is a network communication encryption mechanism, that is, when the communication connection is created, first try to request encryption, if the other party is also Support encryption connection, the connection starts encryption, no authentication is performed during the period; if the encrypted request is attempted to fail, roll back to the plaintext communication mechanism. This encryption does not require both parties to configure, resistant to passive traffic eavesdropping, but unable to defend the initiative attacks such as middleman attacks. Therefore, it cannot replace the complete encryption scheme. When using opportunities to encrypt, users will not see any prompts for connection.
In most Internet security protocols, authentication will be authenticated before the encryption communication is started to prevent intermediary attacks, thereby ensuring communication security. However, this will involve authentication and key management, and must be configured in advance, otherwise security communication cannot be started. This makes the encryption a problem that "is or not", can only be selected between "full security" or "completely unsafe" two extreme options, only when there is no condition, it can only give up encryption, use unsafe plain text connect. This limits the large-scale application encrypted on the Internet, allowing the passive attacker to eavesdropped a large number of Internet traffic.
Opportunity Encryption does not require authentication to use encryption communication mode as much as possible when conditions permit. Although opportunistic encryption can only prevent passive stealing, the active attack of the attacker is powerful (such as a downgrade attack or middleman attack), but it makes large-scale encrypted Internet communication becomes possible, thereby preventing large-scale monitoring, "most When providing a certain degree of security. "
