familymembers
ThefivealgorithmsoftheSHAfamilyareSHA-1,SHA-224,SHA-256,SHA-384,andSHA-512,designedbytheNationalSecurityAgency(NSA)andissuedbytheNationalInstituteofStandardsandTechnology(NIST);itisaUSgovernmentstandard.ThelatterfouraresometimesreferredtoasSHA-2.SHA-1iswidelyusedinmanysecurityprotocols,includingTLSandSSL,PGP,SSH,S/MIME,andIPsec.ItwasonceregardedasthesuccessortoMD5(ahashfunctionthatwaswidelyusedearlier).However,thesecurityofSHA-1isnowseriouslyquestionedbycryptographers;althoughtherehasnotyetbeenaneffectiveattackonSHA-2,itsalgorithmisbasicallystillsimilartoSHA-1;therefore,somepeoplehavebeguntodevelopotheralternativehashalgorithms.
SHA-0and1
Thealgorithmoriginallystatedwasreleasedin1993,calledtheSecureHashStandard(FIPSPUB180).ThisversionisoftencalledSHA-0.ItwaswithdrawnbytheNSAshortlyafteritsrelease,andwasreplacedbyarevisedversionofFIPSPUB180-1(commonlyknownasSHA-1)releasedin1995.TheSHA-1andSHA-0algorithmsonlyhaveaone-bitcyclicshiftinthemessageconversionpartofthecompressionfunction.AccordingtotheNSA,itfixesaweaknessintheoriginalalgorithmthatwouldreducethehashsecurity.However,theNSAdidnotprovideanyfurtherexplanationorproofthattheweaknesshasbeencorrected.Afterwards,theweaknessesofSHA-0andSHA-1havebeenbreached.SHA-1seemstobemoreresistantthanSHA-0.ThissomewhatconfirmstheNSA'soriginalstatementthatthealgorithmwasrevisedtoimprovesecurity.
SHA-0andSHA-1canconvertamaximumof264-bitmessagesintoastringof160-bitmessagedigests;thedesignprincipleissimilartothatdesignedbyMITprofessorRonaldL.RivestThecryptographichashalgorithmMD4andMD5.
SHA-0cracking
OnCRYPTO98,twoFrenchresearchersproposedanattackagainstSHA-0:withinthecomputationalcomplexityof261,youcanFoundacollision(thatis,twodifferentmessagescorrespondtothesamemessagedigest);thisnumberislessthanthe80thpowerof2requiredbythebirthdayattackmethod,thatistosay,thereisanalgorithmthatmakesitssecuritylessthananidealThecomputationalcomplexityofthehashfunctiontoresisttheattack.
In2004,BihamandChenalsodiscoveredtheapproximatecollisionofSHA-0,thatis,twomessagescanbehashedtoalmostthesamevalue;142ofthe162bitsarethesame.TheyalsofoundacompletecollisionofSHA-0(asopposedtoanapproximatecollision),reducingthecomplexityofthe80thpowertothe62thpower.
OnAugust12,2004,Joux,Carribault,Lemuet,andJalbyannouncedamethodtofindacompletecollisionoftheSHA-0algorithm.ThisistheresultofsummarizingtheattacksofChabaudandJoux.Only251computationalcomplexityisrequiredtofindacompletecollision.Theyareusingasupercomputerwith256Itanium2processors,whichconsumesabout80,000CPUman-hours.
OnAugust17,2004,attheCRYPTO2004Rumpmeeting,WangXiaoyun,FengDengguo,LaiXuejia,andYuHongboannouncedthepreliminaryresultsofattackingMD5,SHA-0andotherhashfunctions.ThecomputationalcomplexityoftheirattackonSHA-0is2tothe40thpower,whichmeansthattheirattackresultsarebetterthanthoseofJouxandothers.SeeMD5security.InFebruary2005,WangXiaoyun,YinYiqun,andYuHongbore-publishedthealgorithmtobreaktheSHA-0,andthecollisioncanbefoundwithinthecomputationalcomplexityof2tothe39thpower.
SHA-1cracking
InviewofSHA-0'scrackingresults,expertssuggestthatthosewhoplantouseSHA-1toimplementacryptographicsystemshouldalsoreconsider.AftertheresultsoftheCRYPTOmeetingin2004wereannounced,NISTannouncedthattheywouldgraduallyreducetheuseofSHA-1andreplaceitwithSHA-2.
In2005,RijmenandOswaldpublishedanattackontheweakerversionofSHA-1(53encryptioncyclesinsteadof80):findcollisionswithinthecomputationalcomplexityof2tothe80thpower.
InFebruary2005,WangXiaoyun,YinYiqunandYuHongbopublishedanattackonthefullversionofSHA-1.Onlyacomputationalcomplexityoflessthan2tothe69thpowerisrequiredtofindasetofcollisions..(Usingthebirthdayattackmethodtofindthecollisionrequiresacomputationalcomplexityof2tothe80thpower.)
Theauthorsofthispaperwrote;,Approximatecollision,multi-blockcollisiontechnology,andinformationmodificationtechnologyforfindingcollisionsfromtheMD5algorithm.Withoutthesepowerfulanalysistools,SHA-1cannotbecracked."Inaddition,theauthoralsoshowedthatitencrypts58timesatatime.CirculateSHA-1'sdecryption,andfindasetofcollisionswithin2tothe33thpowerunitoperation.ThepaperonthecompleteattackmethodwaspublishedintheCRYPTOconferenceinAugust2005.
YinYiqunstatedinaninterview:"Generallyspeaking,wehavefoundtwoweaknesses:oneisthatthepre-processingisnotcomplexenough;theotheristhatsomemathematicaloperationsinthefirst20cycleswillCausesunpredictablesecurityproblems."
AttheendoftheCRYPTOmeetingonAugust17,2005,WangXiaoyun,YaoQizhi,andYaoChufengre-publishedamoreefficientSHA-1attackmethod,whichwasabletoperform63timesin2Findthecollisionwithinthecomputationalcomplexity.
Atthe2006CRYPTOconference,ChristianRechbergerandChristopheDeCannièreannouncedthattheycouldfindaSHA-1collisionunderconditionsthatallowedtheattackertodeterminepartoftheoriginalmessage.
Intheacademictheoryofcryptography,ifthecomputationalcomplexityofanyattackmethodislessthanthecomputationalcomplexityrequiredbythebruteforcesearchmethod,itcanberegardedasakindofcrackingforthecryptographicsystem.Method;butthisdoesnotmeanthatthedecryptionmethodhasenteredthestageofpracticalapplication.
Intermsofapplication-levelconsiderations,anewmethodofbreakingsecretshasemerged,suggestingthattheremaybemoreefficientandpracticalimprovedversionsinthefuture.Althoughthesepracticalversionsofdecryptionmethodshavenotyetbeenborn,itisindeednecessarytodevelopstrongerhashalgorithmstoreplacetheoldones.Inadditiontothe"collision"attackmethod,thereisanotherpre-imageattackmethod,inwhichtheoriginalmessageisreversedfromthehashedstring;theseverityofthereversetranslationattackishigherthanthatofthecollisionattack,butIt'salsomoredifficult.Inmanyscenarioswherepasswordhashingisapplied(suchasthestorageofuserpasswords,digitalsignaturesoffiles,etc.),theimpactofcollisionattacksisnotverylarge.Forexample,anattackermaynotonlywanttoforgeanidenticaldocument,butalsowanttomodifytheoriginaldocumentandattachalegalsignaturetofooltheverifierwhoholdstheprivatekey.Ontheotherhand,iftheunencrypteduserpasswordcanbereversedfromtheciphertext,theattackercanusetheobtainedpasswordtologintotheaccountofotherusers,whichisnotallowedinthepasswordsystem.However,ifthereisareversetranslationattack,aslongasthehashedstringofthespecifieduser'spasswordcanbeobtained(usuallystoredinthevideofile,andtheoriginalpasswordinformationmaynotbedisclosed),itispossibletoobtaintheuser'spassword.
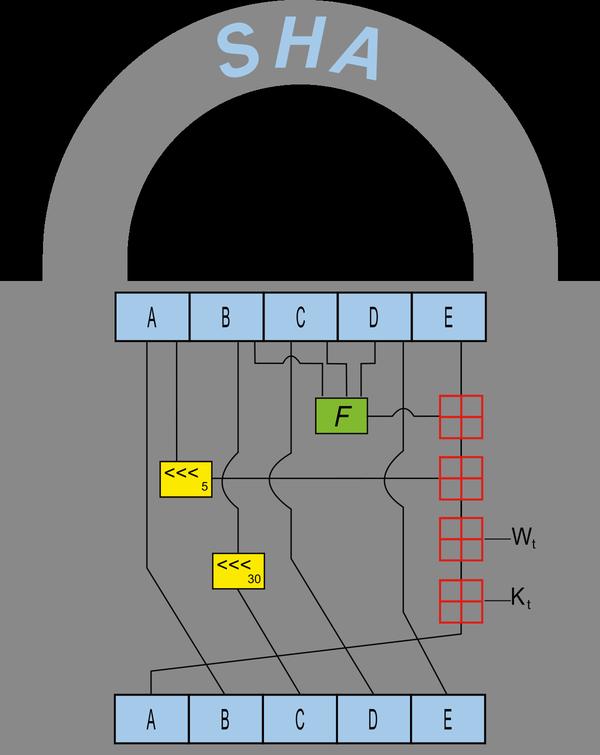
SHA-1algorithm
ThefollowingisthepseudocodeoftheSHA-1algorithm:
Initializevariables:h0:=0x67452301h1:=0xEFCDAB89h2:=0x98BADCFEh3:=0x10325476h4:=0xC3D2E1F0Pre-processing:appendthebit'1'tothemessageappendkbits'0',wherekistheminimumnumber>=0suchthattheresultisamessagelength(in448)conglengthofmessage(beforepre-processing),inbits,as64-bitbig-endianintegerProcessthemessageinsuccessful512-bitchunks:breakmessagesinto512-bitchunksforeachchunkbreakbig-endianintowordsix-wteen32-bitchunks[i],0≤i≤15Extendthesixteen32-bitwordsintoeighty32-bitwords:forifrom16to79w[i]:=(w[i-3]xorw[i-8]xorw[i-14]xorw[i-16])leftrotate1Initializehashvalueforthischunk:a:=h0b:=h1c:=h2d:=h3e:=h4Mainloop:forifrom0to79if0≤thenf≤:=(bandc)or((notb)andd)k:=0x5A827999elseif20≤i≤39f:=bxorcxordk:=0x6ED9EBA1elseif40b≤i≤59fand:=c(bandd)or(candd)k:=0x8F1BBCDCelseif60≤i≤79f:=bxorcxordk:=0xCA62C1D6temp:=(aleftrotate5)+f+e+k+w[i]e:=rotate:30b:left:==Aa:=tempAddthischunk'shashtoresultsofar:h0:=h0+ah1:=h1+bh2:=h2+ch3:=h3+dh4:=h4+eProduce-endthevalue:bigdigest=hash=h0appendh1appendh2appendh3appendh4
SHA-2
NISThasreleasedthreeadditionalSHAvariants,thesethreefunctionsallcorrespondtothemessageLongmessagesummary.Theyarenamedaftertheirdigestlength(calculatedinbits)aftertheoriginalname:SHA-256,SHA-384andSHA-512.Theywerepublishedinthe2001FIPSPUB180-2draft,andthenpassedreviewandcomment.FIPSPUB180-2,whichincludesSHA-1,wasreleasedasanofficialstandardin2002.InFebruary2004,aFIPSPUB180-2changenoticewasissued,addinganadditionalvariantSHA-224",whichisdefinedtocomplywiththekeylengthrequiredfordual-key3DES.
SHA-256andSHA-512areverynewhashfunctions.Theformerdefinesawordas32bits,andthelatterdefinesawordas64bits.TheyusedifferentoffsetsordifferentHowever,infact,thestructureofthetwoisthesame,andonlydiffersinthenumberofloopexecutions.SHA-224andSHA-384aretruncatedversionsoftheaforementionedtwohashfunctions,usingdifferentinitialvaluestodoCalculation.
ThesenewhashfunctionsarenotsubjecttodetailedverificationbypubliccryptographiccommunitieslikeSHA-1,sotheirpasswordsecurityisnotwidelytrustedbyeveryone.GilbertandHandschuhIn2003,Ididsomeresearchonthesenewvariants,claimingthattheydidnotfindanyweaknesses.
Application
SHA-1,SHA-224,SHA-256,SHA-384andSHA-512isusedbytheUSfederalgovernmentthatrequiresasecurehashalgorithm.Theyalsouseothercryptographicalgorithmsandprotocolstoprotectsensitiveunclassifiedinformation.FIPSPUB180-1alsoencouragesprivateorcommercialorganizationstouseSHA-1encryption.Fritz-chipwilllikelyusetheSHA-1hashfunctiontoimplementdigitalcopyrightmanagementonpersonalcomputers.
Thefirsttopromotethesecurehashalgorithmistopublishthemergeddigitalsignaturestandard.
SHAhashfunctionhasbeenusedasthebasisofSHACALblockcipheralgorithm.
See
Encoding
Cryptography
Encryptiontechnology
Algorithm
