Definice
Wormsareacommoncomputervirus.ItusestheInternettoreplicateandspread,andthewayofinfectionisthroughtheInternetande-mail.TheoriginaldefinitionofawormisbecauseintheDOSenvironment,aworm-likethingwillappearonthescreenwhenthevirusbreaksout,anditwilleatthelettersonthescreenandreshapeit.
Awormisaself-containedprogram(orasetofprograms)thatcanspreadcopiesofitsownfunctionsorsomepartsofit(worm)toothercomputersystems(usuallythroughInternetconnection).Pleasenotethatunlikegeneralviruses,awormdoesnotneedtoattachitselftothehostprogram,itisanindependentintelligentprogram.Therearetwotypesofworms:hostwormsandnetworkworms.Thehostcomputerwormsarecompletelycontained(invaded)inthecomputerstheyarerunningon,andusenetworkconnectionstoonlycopythemselvestoothercomputers.Afterthehostcomputerwormsadditsowncopytoanotherhost,itwillterminateit.Byitself(soatanygivenmoment,onlyonecopyofthewormruns),thiswormissometimescalled"hare",andwormsareusuallyspreadthroughthe1434portvulnerability.
Forexample,the"Nimya"virus,whichisveryharmfulinrecentyears,isakindofworm.Inthespringof2007,"PandaBurningIncense"anditsvariantsarealsoworms.ThisvirustakesadvantageoftheloopholesintheMicrosoftWindowsoperatingsystem.Afterthecomputerisinfectedwiththisvirus,itwillcontinuetoautomaticallydialuptotheInternet,andusetheaddressinformationinthefileornetworksharingtospread,ultimatelydestroyingmostoftheuser'simportantdata.
Thegeneralmethodtopreventwormsistouseanti-virussoftwarewithreal-timemonitoringfunctions,andbecarefulnottoopenunfamiliaremailattachmentseasily.
Jak zaútočit
Jak vypadli počítačoví červi
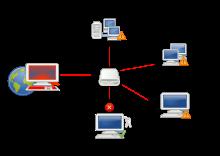
Usevulnerabilitiesinoperatingsystemsandapplicationstoattack
Itisthe"CodeRed"and"Nimya",aswellasthe"coverletter"thatisstillragingtoday.DuetothevulnerabilitiesinInternetExplorer(IFRAMEEXECCOMMAND),emailsinfectedwiththe"Nimya"viruscanbeactivatedwithoutmanuallyopeningtheattachment.Evenbefore,evenmanyantivirusexpertshavealwaysbelievedthatFormailswithvirusattachments,aslongasyoudon’topentheattachments,theviruswillnotbeharmful."CodeRed"usesavulnerabilityintheMicrosoftIISserversoftware(idq.dllremotebufferoverflow)tospread,whiletheSQLWormKingvirususesavulnerabilityinMicrosoft'sdatabasesystemtocarryoutalarge-scaleattack.
Metody různorodého přenosu
Například virus "Nimya" a "krycí dopis", dostupné metody přenosu zahrnují soubory, e-maily, webové servery, sdílení sítě a brzy.
Technologie výroby nových virů
Differentfromtraditionalviruses,manynewvirusesareimplementedusingthelatestprogramminglanguageandprogrammingtechnology,andareeasytomodifytoproducenewvariants.Soastoescapethesearchofanti-virussoftware.Inaddition,thenewvirususestechnologiessuchasJava,ActiveX,andVBScript,whichcanbelurkinginHTMLpagesandtriggeredwhenbrowsingtheInternet.
V kombinaci s hackerskou technologií
Taketheredcodeasanexample,aroot.exewillbegeneratedunder\scriptsinthewebdirectoryoftheinfectedmachine,whichcanexecuteanycommandremotely,therebyEnablehackerstoenteragain.
Onefeaturethatwormsdifferfromordinaryvirusesisthatwormscanoftenexploitvulnerabilities.Thevulnerabilitiesordefectsherecanbedividedintotwotypes,namelysoftwaredefectsandman-madedefects.Softwaredefects,suchasremoteoverflow,automaticexecutionvulnerabilitiesinMicrosoftIEandOutlook,etc.,requirethecooperationofsoftwarevendorsanduserstocontinuouslyupgradethesoftware.Man-madedefectsmainlyrefertothenegligenceofcomputerusers.Thisistheso-calledsocialengineering.Whenreceivingacoverletteremailwithavirus,mostpeopleclickonitwithcuriosity.Forenterpriseusers,thethreatsaremainlyfocusedonthesecurityofserversandlarge-scaleapplicationsoftware,whileforindividualusers,theyaremainlytopreventthesecondtypeofflaw.
Červ, který představuje přímou hrozbu pro jednotlivé uživatele
Amongthewormsanalyzedabove,onlysystemswithspecificMicrosoftcomponentsareattacked,whilethemajorityofindividualusersareattacked.Inotherwords,IIS(Microsoft'sInternetserverprogramthatallowswebservicestobeprovidedontheInternet)orahugedatabasesystemwillnotbeinstalled.Therefore,theabove-mentionedviruseswillnotdirectlyattackthecomputersofindividualusers(ofcourse,theycanindirectlyaffectthenetwork).However,thewormsanalyzednextarethemostthreateningtoindividualusers,andatthesametimethemostdifficulttoeradicate,causinggreaterlosses.
Forindividualusers,themostthreateningwormsarespreadbye-mailandmaliciouswebpages.
Forwormsthatusee-mailtospread,theyusuallyuseavarietyofdeceptivemethodstoenticeuserstoclicktospread.Amaliciouswebpageisexactlyahacker-destroyingcodeprogram,whichisembeddedinthewebpage.Whenauseropensawebpagecontainingaviruswithoutknowingit,theviruswillbreakout.Theprincipleofthisviruscodeinlaytechnologyisnotcomplicated,soitwillbeusedbymanyunscrupulousattempts.Onmanyhackerwebsites,therehavebeenforumsaboutthetechnologyofusingwebpagestodestroythetechnology,andprovidethedownloadofthedestroyingprogramcode,thuscausingmaliciousness.Theproliferationofwebpageshasalsocausedmoreandmoreuserstosufferlosses.
Formaliciouswebpages,vbscriptandjavascriptprogrammingareoftenused.Becausetheprogrammingmethodisverysimple,itisverypopularontheInternet.
Vbscriptandjavascriptareparsedandexecutedbywsh(WindowsScriptingHost)oftheMicrosoftoperatingsystem.Becauseofitsverysimpleprogramming,suchscriptvirusesarespreadingwildlyontheInternet.Iwormvirusisakindofvbsscriptvirus,andthendisguisedasanemailattachmenttoenticeuserstoclicktorun.Whatisevenmorefrighteningisthatsuchvirusesappearintheformofsourcecode.Peoplewhoknowalittleaboutscriptprogrammingcanmodifytheircodetoformvariousvariants.
Osobní bezpečnostní opatření
Preventivní opatření pro osobní uživatele proti červům
Throughtheaboveanalysisandintroduction,wecanknowthatvirusesarenotterrible.Networkwormsattackindividualusersmainlythroughsocialengineering,ratherthanexploitingsystemvulnerabilities!Therefore,topreventsuchviruses,youneedtopayattentiontothefollowingpoints:
Kupte si vhodný antivirový software
Thedevelopmentofnetworkwormshasmadethetraditionalanti-virussoftware"file-levelreal-timemonitoringsystem"Outdated,anti-virussoftwaremustdeveloptoreal-timememorymonitoringandreal-timeemailmonitoring!Inaddition,inthefaceofunpredictablewebpageviruses,usersalsohavehigherandhigherrequirementsforanti-virussoftware!
Často aktualizujte databázi virů
Theanti-virussoftwarechecksandkillsvirusesbasedonthevirussignature,andvirusesemergeinendlesslyeveryday,especiallyintheInternetage.Thespreadspeedisfastandtherearemanyvariants,sothevirusdatabasemustbeupdatedatanytimetobeabletocheckandkillthelatestvirus.
Zlepšení antivirového povědomí
Neklikejte na neznámé stránky snadno, může obsahovat škodlivý kód!
WhenIEisrunning,click"Tools→InternetOptions→Security→InternetZoneSecurityLevel"tochangethesecuritylevelfrom"Medium"to"High".BecausethistypeofwebpageismainlyActiveXorApplet,JavaScriptwebpagefilescontainingmaliciouscode,allActiveXplug-insandcontrols,Javascripts,etc.areprohibitedintheIEsettings,whichcangreatlyreducethechanceofbeinginfectedbywebpagemaliciouscodes.Thespecificsolutionis:Click"Tools"→"InternetOptions"intheIEwindow,selectthe Otevřete dialogové okno „Zabezpečení“ a poté klikněte na tlačítko „Vlastní úroveň“ a zobrazí se dialogové okno „Nastavení zabezpečení“. Vyberte „Zakázat“ pro všechny ActiveX plug-iny a ovládací prvky a všechny možnosti související s Javou.
Nekontrolujte neznámé e-maily náhodně
especiallyemailswithattachments.Becausesomevirusemailscantakeadvantageofvulnerabilitiesinieandoutlooktoexecuteautomatically,computerusersneedtoupgradeieandoutlookprograms,aswellasothercommonlyusedapplications.
Byl objeven nejnovější červí „maskovaný host“, který může uniknout soukromí
Virusunikátnost
Similaritiesanddifferencesbetweenwormvirusesandgeneralviruses
Awormisalsoavirus,soithasthecommoncharacteristicsofavirus.Thegeneralvirusisparasitic,itcanwriteitsowninstructioncodeintothebodyofotherprogramsthroughtheexecutionofitsowninstructions,andtheinfectedfileiscalledthe"host",forexample,theexecutablefileunderwindowsTheformatispeformat(PortableExecutable).Whenthepefileneedstobeinfected,anewsectioniscreatedinthehostprogram,theviruscodeiswrittentothenewsection,theprogramentrypointismodified,etc.,sothatwhenthehostprogramisexecuted,Thevirusprogramcanbeexecutedfirst,andafterthevirusprogramhasfinishedrunning,controlisgiventothehost'soriginalprograminstructions.Itcanbeseenthatvirusesmainlyinfectfiles.Ofcourse,therearealsolink-typeviruseslikeDIRIIandbootsectorviruses.Thebootsectorvirusinfectsthebootsectorofthedisk.Ifafloppydiskisinfected,afterthefloppydiskisusedonothermachines,itwillalsoinfectothermachines.Therefore,themethodoftransmissionisalsoafloppydisk.
Wormsgenerallydonotusethepeformattoinsertfiles.Instead,theycopythemselvesandspreadintheInternetenvironment.Theinfectionabilityofthevirusismainlyaimedatthefilesysteminthecomputer,andtheinfectionofwormsThetargetisallcomputersintheInternet.Sharedfolders,e-mails,maliciouswebpagesinthenetwork,andalargenumberofvulnerableservershavebecomegoodwaysforwormstospreadundertheconditionoflocalareanetworks.ThedevelopmentoftheInternetalsoallowswormstospreadacrosstheworldwithinafewhours!Andtheactiveaggressivenessandsuddenexplosivenessofwormswillmakepeoplefeelhelpless!
AnythingthatcancausecomputerfailuresanddestroycomputerdataTheprogramsarecollectivelyreferredtoascomputerviruses.Sointhissense,awormisalsoavirus!Networkwormvirus,asacomputerprogramthatisserioustotheInternet,itsdestructivepowerandcontagioncannotbeignored.Unliketraditionalviruses,wormsusecomputersascarriersandtheInternetastheirtargetofattack!Inthisarticle,wormsaredividedintotwocategoriesforcorporatenetworksandindividualusers,andthecharacteristicsofwormsandsomepreventivemeasuresarediscussedfrombothcorporateusersandindividualusers!
PreventsystemvulnerabilitiesfromwormsThebestwaytoinfringeistopatchthecorrespondingsystem.Youcanusethe"VulnerabilityScanning"toolofRisingAnti-Virus.Thistoolcanguideuserstopatchandperformcorrespondingsecuritysettingstocompletelyeliminatevirusinfection.
Disseminationviae-mailhasbeenoneofthemethodsfavoredbyvirusauthorsinrecentyears,suchas"EvilEagle"and"NetworkSky"areallmailwormsthatareveryharmful.Suchvirusesoftenmutatefrequentlyandinlargenumbers.Afterusersarepoisoned,theyoftencausedataloss,personalinformationtheft,andslowsystemoperation.
Thebestwaytopreventmailwormsistoraiseyourownsecurityawarenessanddonotopenemailswithattachmentseasily.Inaddition,enablingthe"emailsendingmonitoring"and"emailreceivingmonitoring"functionsoftheRisinganti-virussoftwarecanalsoimproveyourabilitytoprotectagainstvirusemails.
Since2004,chatsoftwaresuchasMSNandQQhasbecomeoneofthewaysforwormstospread.The"SexyRoastChicken"virusspreadthroughMSNsoftwareandswepttheworldinashortperiodoftime,causingabnormaloperationofsomenetworksinmainlandChina.
Forordinaryusers,oneofthemainmeasurestopreventchatwormsistoimprovesecurityawareness.Anyfilesentthroughchatsoftwaremustbeconfirmedbyfriendsbeforerunning;donotclickchatatwillThenetworklinksentbythesoftware.
Withthedevelopmentofnetworkandviruswritingtechnology,moreandmorewormsusemultiplemethods.Forexample,somewormsspreadthroughe-mailandatthesametimeusesystemvulnerabilitiestoinvadeusersystems.Otherviruseswillspreadthroughmultiplechannelssuchasemailandchatsoftwareatthesametime.
Vývojový trend
Trend ničení a vývoje červů
In1988,awormviruswrittenbyMorris,agraduatestudentofCORNELLUniversityintheUnitedStates,spreadandcausedthousandsofcomputers.Whentheshutdownwasstopped,thewormvirusbegantoappearonthenetwork;andthelaterCodeRed,whentheNimdaviruswascrazy,causedbillionsofdollarsinlosses;onJanuary26,2003,Beijingtime,akindof"2003WormKing"Computervirusesspreadrapidlyandattackedtheworld,causingseriousblockagesintheInternet.Theparalysisofthedomainnameserver(DNS)asthemainfoundationoftheInternethascausednetizenstobrowseInternetpagesandsendandreceiveemails.ThespeedofInternetusershasgreatlysloweddown.Atthesametime,theoperationofbankATMsInterruption,theoperationoftheonlinebookingsystemsuchasairticketsisinterrupted,andthecollectionandpaymentsystemssuchascreditcardsaremalfunctioning!Expertsestimatethatthedirecteconomiclosscausedbythisvirusisatleast1.2billionUSdollars!
Název viru
Doba trvání
Způsobil ztráty
Morethan6000computerswereshutdownin1988,andthedirecteconomiclossofMorrisWormreached96millionUSdollars!
BeautyKiller1999Governmentdepartmentsandsomelargecompaniesurgentlyshutdowntheirwebservers,causingeconomiclossesofmorethan1.2billionU.S.dollars!
Počítače Alotofuser byly infikovány od května 2000 se ztrátami přesahujícími 10 miliard amerických dolarů.
CodeRed'snetworkwasparalyzedinJuly2001,andthedirecteconomiclossexceededUS$2.6billion.
AlargenumberofvirusemailsblockedtheserverinthecoverlettersinceDecember2001,andthelossreachedtensofbillionsofUSdollars
SqlwormkinginJanuary2003,thenetworkwaslargelyparalyzed,bankATMoperationswereinterrupted,andthedirecteconomiclossexceeded2.6billionUSdollars.Andcausedhugeeconomiclosses!
