Въведение
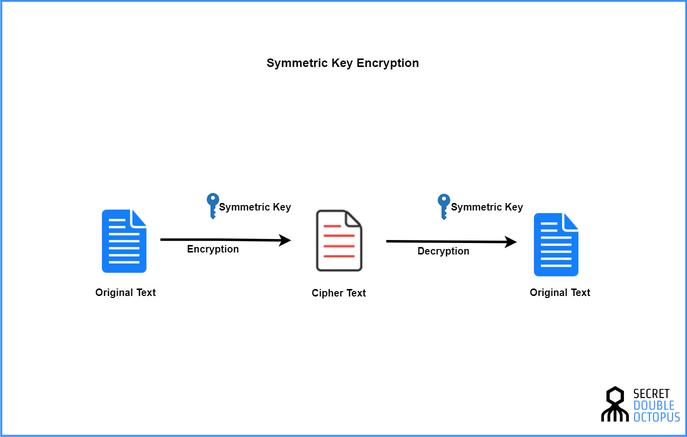
Symmetricencryption(alsocalledprivatekeyencryption)referstoanencryptionalgorithmthatusesthesamekeyforencryptionanddecryption.Sometimescalledtraditionalcryptographicalgorithm,thatis,theencryptionkeycanbecalculatedfromthedecryptionkey,andthedecryptionkeycanalsobecalculatedfromtheencryptionkey.Inmostsymmetricalgorithms,theencryptionkeyandthedecryptionkeyarethesame,sothisencryptionalgorithmisalsocalledasecretkeyalgorithmorasinglekeyalgorithm.Itrequiresthesenderandreceivertoagreeonakeybeforecommunicatingsecurely.Thesecurityofthesymmetricalgorithmdependsonthekey.Leakingthekeymeansthatanyonecandecryptthemessagestheysendorreceive.Therefore,theconfidentialityofthekeyisveryimportanttothesecurityofcommunication.
Характеристика
Thecharacteristicsofthesymmetricencryptionalgorithmarethatthealgorithmisopen,theamountofcalculationissmall,theencryptionspeedisfast,andtheencryptionefficiencyishigh.
Thedisadvantageisthatbothpartiesinthetransactionusethesamekey,andsecuritycannotbeguaranteed.Inaddition,everytimeeachpairofusersusesasymmetricencryptionalgorithm,theyneedtouseauniquekeythatothersdon'tknow.Thiswillincreasethenumberofkeysownedbybothsendersandreceiversexponentially,andkeymanagementbecomesaburdenonusers.Symmetricencryptionalgorithmsaremoredifficulttouseondistributednetworksystems,mainlybecausekeymanagementisdifficultandtheusecostishigh.Comparedwiththepublickeyencryptionalgorithm,thesymmetricencryptionalgorithmcanprovideencryptionandauthenticationbutlacksthesignaturefunction,whichreducesthescopeofuse.SymmetricencryptionalgorithmswidelyusedincomputerprivatenetworksystemsincludeDESandIDEA.AESadvocatedbytheNationalBureauofStandardsisabouttoreplaceDESasanewstandard.
Theadvantageofthesymmetricencryptionalgorithmliesinthehighspeedofencryptionanddecryptionandthedifficultyofcrackingwhenusinglongkeys.Assumingthattwousersneedtousesymmetricencryptiontoencryptandthenexchangedata,theusersneedatleast2keysandexchangethem.Iftherearenusersintheenterprise,theentireenterpriseneedsn×(n-1)keysintotal.Thegenerationanddistributionofkeyswillbecomeanightmareforcorporateinformationdepartments.Thesecurityofthesymmetricencryptionalgorithmdependsonthepreservationoftheencryptionkey,butitisimpossibletorequireeveryoneintheenterprisewhoholdsthekeytokeepthesecret.Theyusuallyleakthekeyintentionallyorunintentionally—ifoneThekeyusedbytheuserisobtainedbytheintruder,andtheintrudercanreadallthedocumentsencryptedbytheuser'skey.Iftheentireenterprisesharesanencryptionkey,theconfidentialityoftheentireenterprisedocumentwillbeimpossibletotalkabout.
Специфични алгоритми
Основно включват DESалгоритъм, 3DESалгоритъм, TDEAалгоритъм, Blowfishalgorithm, RC5алгоритъм, IDEAалгоритъм.
Hereisabriefintroductiontotheencryptionalgorithmbasedon"symmetrickey".
Алгоритмите за криптиране, базирани на "симетричен ключ", включват главно DES, TripleDES, RC2, RC4, RC5 и Blowfish.
Symmetrickey:DESTripleDESалгоритъм
TheDESalgorithmturnsa64-bitplaintextinputblockintoaciphertextoutputblockwithadatalengthof64bits.Amongthem,8bitsareparitybits,andtheother56bitsarethelengthofthepassword.First,DESrecombinestheinput64-bitdatablockbybit,anddividestheoutputintotwoparts,L0andR0,eachpartis32bitslong,andisreplacedbeforeandafter.Finally,L0outputs32bitsontheleftandR0outputs32ontheright.Accordingtothisrule,after16iterations,L16andR16areobtained,whichareusedasinput,andtheinversepermutationoppositetotheinitialpermutationisperformedtoobtaintheciphertextoutput.
TheDESalgorithmhasextremelyhighsecurity.Sofar,inadditiontotheexhaustivesearchmethodtoattacktheDESalgorithm,nomoreeffectivemethodhasbeenfound,andtheexhaustionofthe56-bitlongkeyThespaceis2^56,whichmeansthatifacomputercandetect1millionkeyspersecond,itwilltakenearly2285yearstosearchforallkeys.Therefore,theDESalgorithmisveryreliable.Encryptionmethod.
Симетричен ключ: RCалгоритъм
TheprincipleoftheRC4algorithmis"confusion",whichincludestwoparts:initializationalgorithmandpseudo-randomsub-ciphergenerationalgorithmIntheprocessofinitialization,themainfunctionofthekeyistorandomlyscramblea256-byteinitialnumbercluster.Differentnumberclusterscangetdifferentsub-keysequencesafterbeingprocessedbythepseudo-randomsub-ciphergenerationalgorithm.AfterperforminganexclusiveORoperation(XOR)ontheobtainedsubkeysequenceandtheplaintext,theciphertextisobtained.
BecausetheRC4algorithmencryptionusestheexclusiveORmethod,oncethesub-keysequenceisrepeated,theciphertextmaybecracked,butthereisnoRC4withakeylengthof128bits.Thereisapossibilityofduplication,soRC4isalsooneofthemostsecureencryptionalgorithmsatpresent.
Symmetrickey:BlowFishalgorithm
BlowFishalgorithmisa64-bitblockandvariablekeylengthblockcipheralgorithm,thealgorithmisnon-patent.
TheBlowFishalgorithmusestwo"boxes":pbox[18]andsbox[4256].TheBlowFishalgorithmhasacoreencryptionfunction.Thisfunctioninputs64-bitinformation,andoutputsitintheformof64-bitciphertextaftercalculation.EncryptinginformationwiththeBlowFishalgorithmrequirestwoprocesses:keypreprocessingandinformationencryption.TheoriginalkeyspboxandsboxoftheBlowFishalgorithmarefixed.Toencryptamessage,youneedtoselectakey,andusethiskeytotransformthepboxandsboxtoobtainthekey_pboxandkey_sboxusedinthenextstepofinformationencryption.
BlowFishalgorithmdecryptionalsorequirestwoprocesses:keypreprocessingandinformationdecryption.Theprocessofkeypreprocessingisexactlythesameasthatofencryption.Theprocessofinformationdecryptionistousethekey_pboxinthereverseorderoftheinformationencryptionprocess.
Режим на приложение
Режим на криптиране (английско име и съкращение)
Китайско име
Електронна кодова книга (ECB)
Режим на електронна кодова книга
CipherBlockChaining (CBC)
Режим на блокиране на парола
CipherFeedbackMode (CFB)
EncryptedFeedbackMode
OutputFeedbackMode (OFB)
OutputFeedbackMode
ECB:Themostbasicencryptionmode,whichiscommonlyunderstoodencryption.Thesameplaintextwillalwaysbeencryptedintothesameciphertextwithoutaninitialvector.Itisvulnerabletocodebookreplayattacksandisrarelyusedingeneral.
CBC:Beforetheplaintextisencrypted,itneedstobeXORedwiththepreviousciphertextandthenencrypted,soaslongasyouchooseadifferentinitialvector,thesameciphertextwillbeencryptedtoformadifferentciphertext.ThisisCurrentlythemostwidelyusedmode.TheciphertextencryptedbyCBCiscontext-dependent,buterrorsintheplaintextwillnotbepassedontosubsequentpackets,butifonepacketislost,allsubsequentpacketswillbeinvalidated(synchronizationerrors).
CFB:Similartoaself-synchronizingsequencecipher,afterblockencryption,theciphertextandplaintextareshiftedandXORedaccordingto8-bitgroups,andtheoutputisreturnedtotheshiftregisteratthesametime.TheadvantagecanbeassmallasbyteEncryptionanddecryptioncanalsobenbits.CFBisalsocontext-dependent.InCFBmode,anerrorintheplaintextwillaffectthesubsequentciphertext(errordiffusion).
OFB:Runtheblockcipherasasynchronoussequencecipher,similartoCFB,butOFBusesthepreviousn-bitciphertextoutputpackettobefedbacktotheshiftregister,OFBhasnoerrorpropagationproblem.
